A major leak has shaken RemoteCOM, a company dedicated to selling spyware aimed at monitoring individuals under parole and probation. This week, the breach made its way to a known cybercrime forum, exposing highly sensitive information related to employees within the corrections system and those under judicial supervision.
RemoteCOM proudly claims to be “the premier computer, smartphone and tablet monitoring service for the management of pretrial, probation, and parole clients.” Their technology is said to facilitate the work of parole and probation officers across 49 states!
The leaked data includes a training manual for RemoteCOM’s software called SCOUT, revealing that the spyware can be used for tracking not just sex offenders, but also sex traffickers, terrorists, and gang members.

SCOUT’s features are alarming, as it can monitor keystrokes, emails, chat messages, location data, and other activities directly on devices. It even allows taking screenshots, blocks access to specific websites, and sends alerts if certain keywords get typed.
The hacker, going online by the name of “wikkid,” mentioned that this breach was one of their easiest attempts ever. While Straight Arrow News notified RemoteCOM about the data leak with a phone call on Thursday, the company did not respond to the warning.
This data breach revealed the names and addresses of various probation agencies using RemoteCOM’s services. Moreover, it included contact information such as email addresses and phone numbers for over 800 probation supervisors, and exposed the contact details of more than 80 current and former RemoteCOM employees.
Eva Galperin, the director of security at the Electronic Frontier Foundation, flagged this incident as a troubling indication of the vulnerability associated with using monitoring technologies. She stated to SAN that this oversight is especially serious for a company handling sensitive government contracts and personal data.
Exposed Personal Information
Affected files contain extensive data on 6,896 individuals working within the criminal justice system who rely on RemoteCOM’s services. Each file entry lists a person’s name, phone number, work address, email, unique ID, and job title.
Another alarming file, d “clients,” catalogs information on nearly 14,000 supervised individuals. This database shows offenders’ names, email addresses, IPs, home addresses, and phone numbers next to those of their probation officers.
One entry pointed out an offender for whom SCOUT software was installed on devices that belonged to their sister-in-law and fiancée. There’s even a discussion in a Reddit group focused on sex offender support, emphasizing here that spyware really needs to be installed on every device an offender can reasonably access.
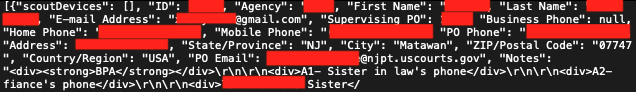
“Your [probation officer] will tell you how many devices it needs to cover,” mentioned a user from the group. “Then, you’ll contact RemoteCOM to arrange the installation remotely.”
From what’s revealed in the documents, it seems offenders are charged $50 for each computer where SCOUT is installed. Adding to this, phone installations will set them back by $30, along with a recurring $35 monitoring fee every month.
The leaked data ultimately reveals a range of offenses, with indicators highlighting whether individuals monitored had previous allegations concerning sex offenses, weapons, terrorism, narcotics, stalking, domestic violence, and other serious infractions. Those termed “tech-savvy” add yet another layer of scrutiny.
Insider Alerts
A wealth of more than 380,000 alerts sent to probation officers provides a peek into the capabilities of SCOUT. In one scenario, an offender categorized with terrorism and weapons charges triggered an alert for “Notable Information” detected on their device.
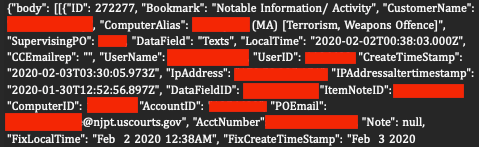
On other occasions, the alerts hinted at possible parole or probation violations. However, the data stopped short of detailing the specific triggers for those alerts.
A small sample of unpublished information shared with SAN showed different keywords flagged by SCOUT, with an offender alert notes sounding the alarm after typing the term “Nazi,” while another individual’s alert was triggered merely by typing “sex.”
The cautionary tale of RemoteCOM’s breach serves as a significant wake-up call about the mechanical vulnerabilities within security surrounding even the most sensitive monitoring technologies.